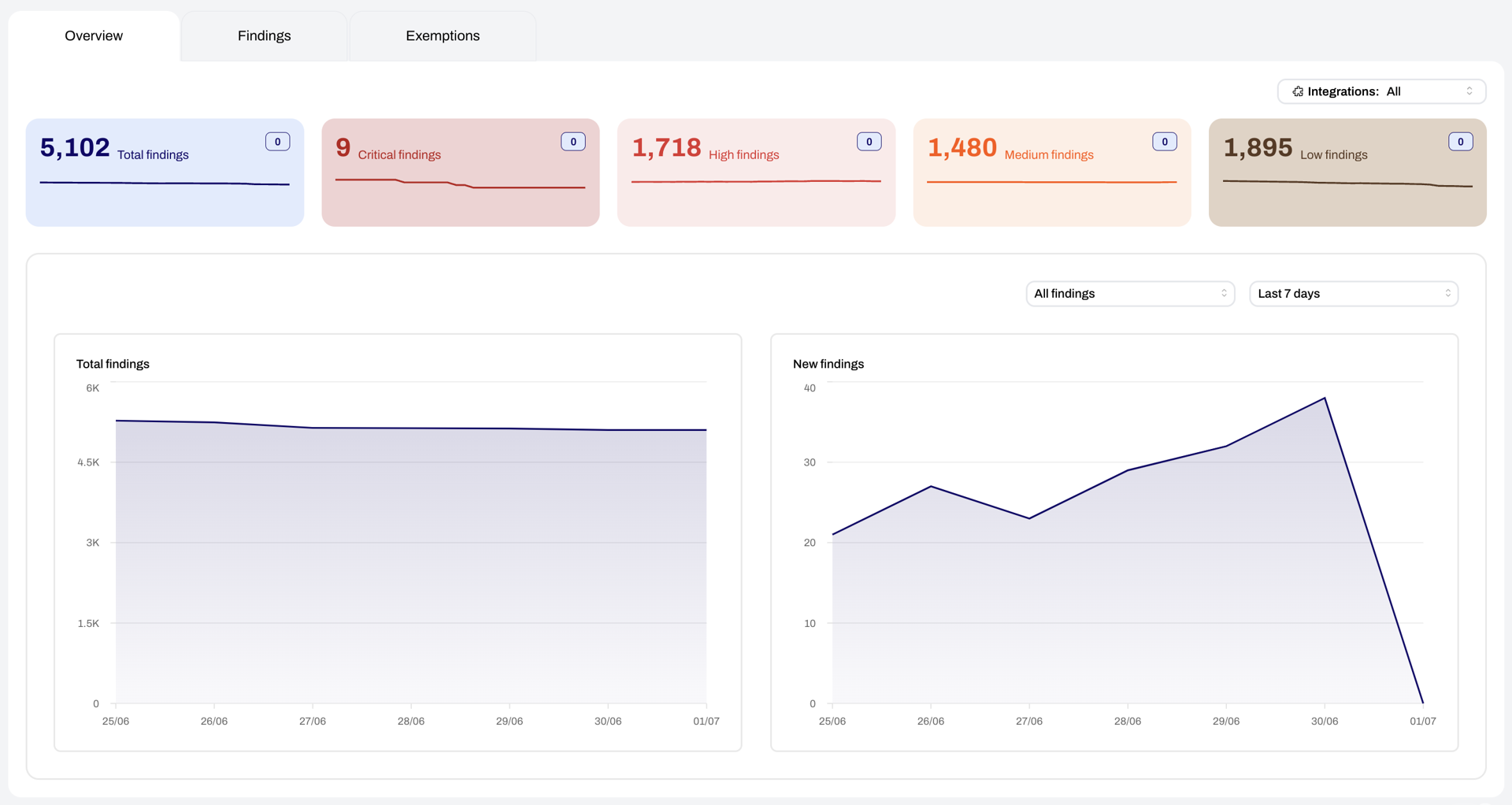
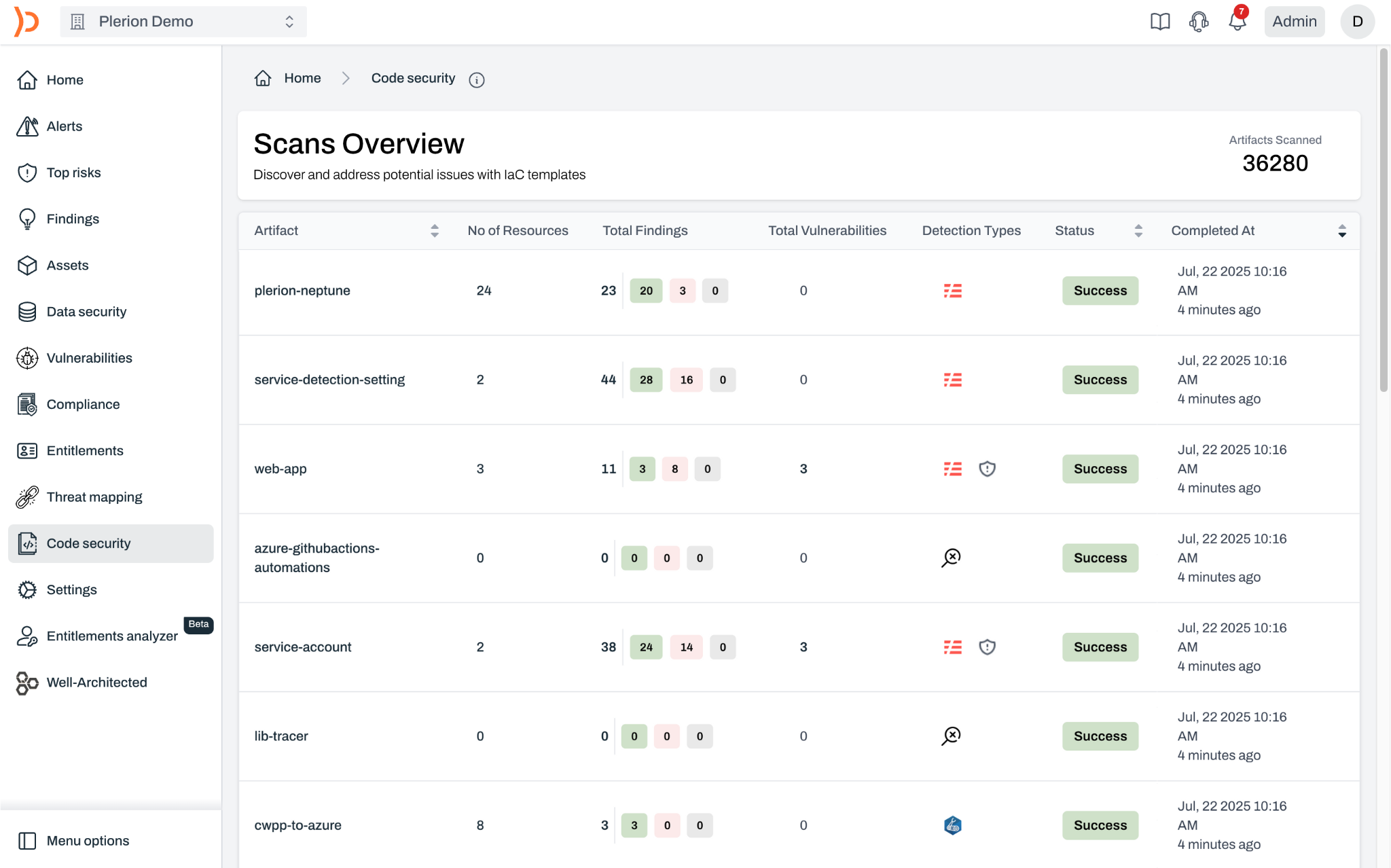
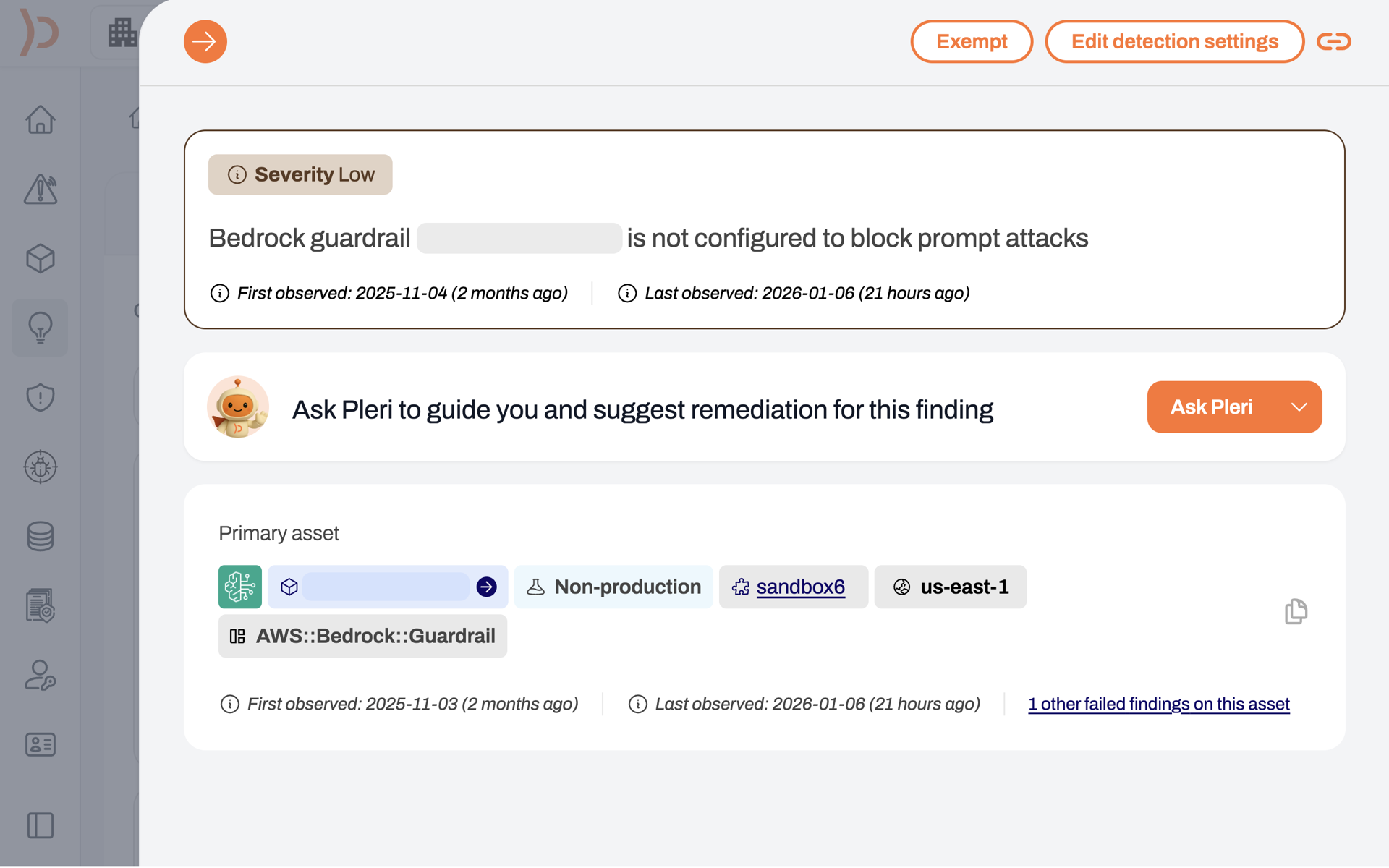
Attackers move around the cloud by compromising identities and abusing trust relationships. We list every identity, every resource, and every IAM policy to show you who has access to what in your cloud environment. Use this to limit the blast radius of attacks or demonstrate compliance to auditors.